HackTheBox has an interesting way of handling account creation – rather than it generating an invite link for you, you have to figure out how to generate one yourself.
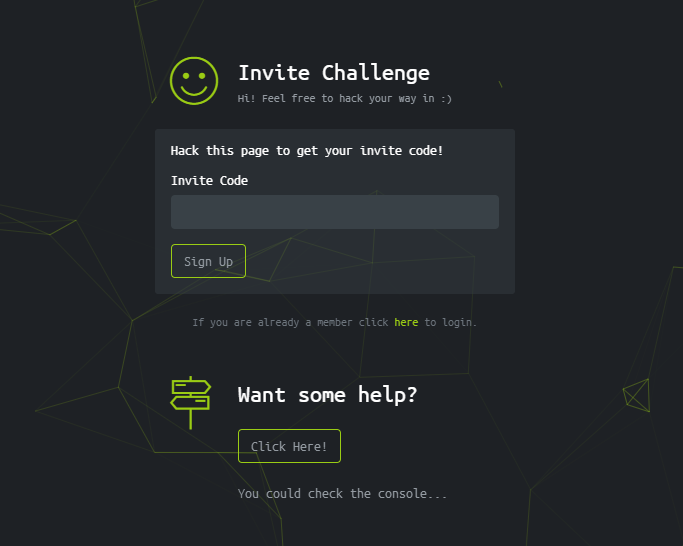
The first thing I did, naturally, was click the help button. I figured it wouldn’t hurt much, but I had already assumed that this challenge would take place using browser developer tools.
In the console, we can see right away that the first step is given.

Following the image, I went to check out the sources of the site. In here, there are a couple js files. One stands out in particular due to the comment attached to it:
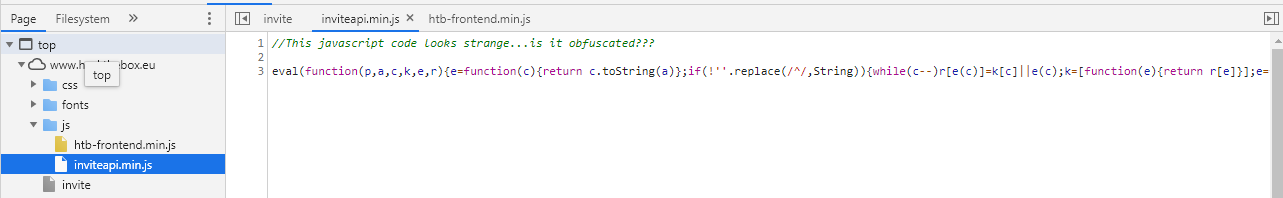
I’ve dealt with obfuscated code in a lot of reverse engineering challenges in the past, so I went to a site I know pretty well: https://lelinhtinh.github.io/de4js/
It’s a JavaScript deobfuscator and unpacker that has a ton of different options. I’ve never had JS code that wasn’t deobfuscated using this tool.
Sure enough, after selecting the Eval method, I got the following JS:
function makeInviteCode() {
$.ajax({
type: "POST",
dataType: "json",
url: '/api/invite/how/to/generate',
success: function (a) {
console.log(a)
},
error: function (a) {
console.log(a)
}
})
}
This didn’t appear to be very useful, but I put the function name into the console to run it. Doing this is something I’m pretty used to seeing, especially since a couple of my own challenges on CyberCrack use console functions.
Here’s where I made my first mistake: Instead of entering makeInviteCode(), I entered makeInviteCode();
The difference doesn’t seem large, but the semicolon actually changed the output drastically. I tried doing some research on the developer console to determine why this is, but fell short of any answers. Again, I know from my own experience that this is usually the case, but I haven’t learned why yet.
Anyways, after entering the function properly, I got the following output:
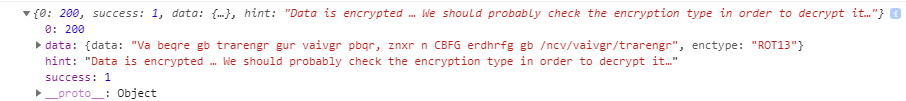
The data that is returned by the function is encrypted in ROT13. Following that trail to decrypt the data returns this:
In order to generate the invite code, make a POST request to /api/invite/generate
Typically, I use curl to make easy POST requests. It’s been a while since I used it though, and I was rusty. After some Googling, I came up with the following command but failed to have a result:
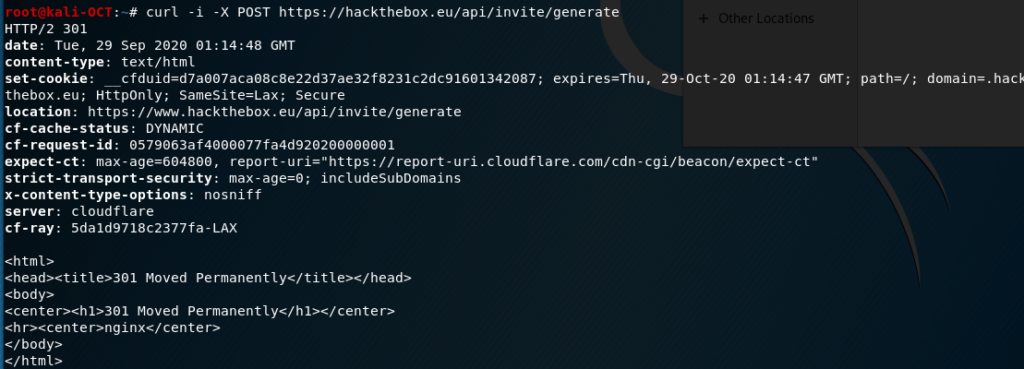
So why did this fail? Why a 301?
Can you spot the mistake?
I made an easy mistake of forgetting the “www” before the domain name. After doing such, I received my invite code. But wait! It’s still encoded.
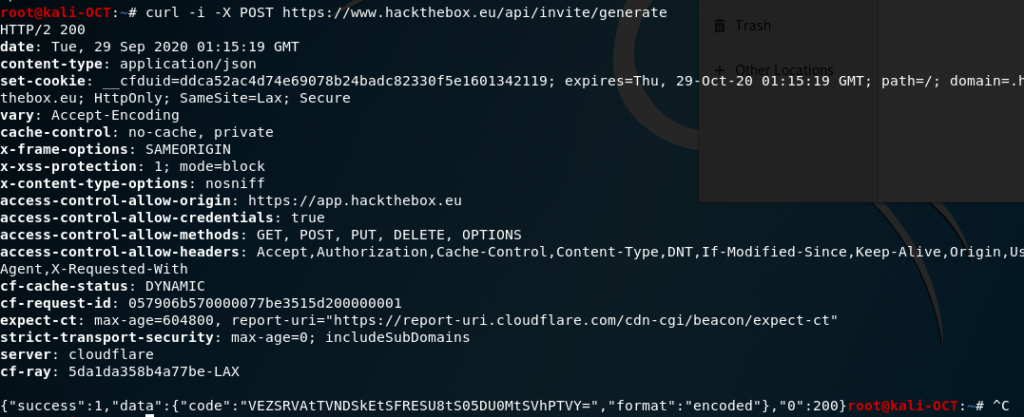
As I’ve talked about in various write-ups, it’s easy to tell Base64 by the padding at the end. After decoding the Base64, I received my invitation code to officially make a profile on HTB.